Evaluating Cyber Threats in Contemporary Conflicts
Introduction
The digital age has redefined the battlefield, with cyberspace emerging as a critical domain in modern conflicts. Cyber Threat Analysis (CTA) plays a pivotal role in understanding how adversaries exploit information technologies for warfare, espionage, and disruption. Recent conflicts, including the war in Ukraine and the Hamas attack on Israel, highlight the significance of CTA in identifying vulnerabilities and bolstering digital security.
What is Cyber Threat Analysis (CTA)?
CTA involves collecting, analyzing, and interpreting data on potential cyber threats to understand their nature, methods, and objectives. By leveraging this intelligence, organizations can shift from reactive to proactive strategies, effectively countering cybercriminals. Key components of CTA include:
Identifying Threat Actors: Understanding who is behind cyberattacks.
Analyzing Tactics and Tools: Examining the techniques and technologies used in attacks.
Assessing Vulnerabilities: Highlighting weaknesses in digital infrastructures.
Case Studies: Ukraine and Israel
Ukraine:
The Russia-Ukraine conflict has been a testing ground for cyber warfare. Russian operations have targeted Ukraine’s critical infrastructure, government institutions, and communication systems.
Reports indicate an increase in hybrid attacks combining physical and digital warfare, highlighting the necessity for robust CTA strategies.
Israel:
The Hamas attack on Israel underscores the rise of asymmetric cyber warfare, where non-state actors employ cyberspace for propaganda, disinformation, and sabotage.
Despite significant concerns, cyber operations during this conflict have been less impactful than anticipated, potentially due to a lack of preparation by adversaries.
Challenges in Modern Cyber Warfare
Escalation Risks: Misinterpretation of cyber incidents can lead to unintended geopolitical consequences.
Evolving Tactics: Threat actors continually adapt their strategies, making it imperative for organizations to stay ahead.
Resource Limitations: Many nations and organizations lack the resources to implement comprehensive CTA frameworks.
Recommendations for Strengthening Cybersecurity
Invest in Cyber Threat Intelligence (CTI): Equip organizations with tools and expertise to analyze and counter cyber threats effectively.
Enhance International Cooperation: Foster collaboration between nations to share intelligence and combat cross-border cyber threats.
Improve Awareness and Training: Educate staff and stakeholders about emerging cyber risks and prevention strategies.
Adopt Proactive Security Measures: Implement software updates, network monitoring, and penetration testing to identify and mitigate vulnerabilities.
Conclusion
Modern conflicts demonstrate that cyberspace is a vital arena for both offensive and defensive operations. Cyber Threat Analysis is indispensable for safeguarding critical infrastructure, national security, and private interests. By adopting proactive strategies and fostering international cooperation, organizations can better navigate the complexities of cyber warfare and protect against escalating digital threats.
Tags: Cyber Threat Analysis, Cybersecurity, Modern Conflicts, Ukraine, Israel, Cyber Warfare, Cyber Intelligence, Digital Security
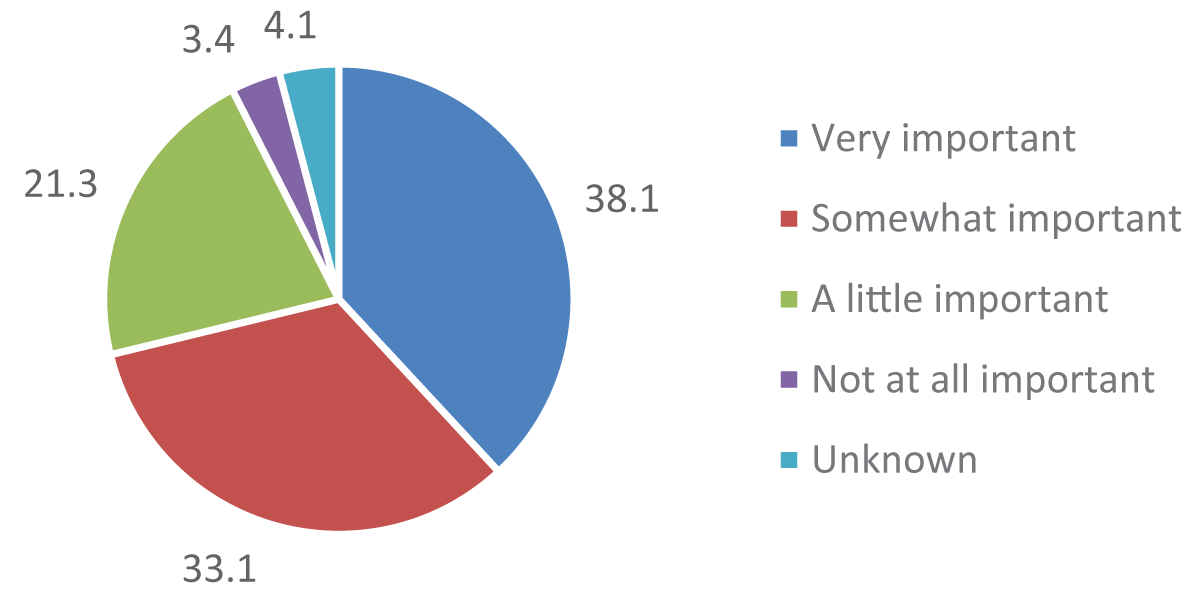
The Figure shows the CTI Survey (2023) for the importance of geopolitics in developing intelligence requirements. Source: SANS 2023 CTI Survey.
