Strengthening IoT Network Protocols: A Model Resilient Against Cyber Attacks
Enhancing IoT Security: A Robust Protocol Against Cyber Threats
The rapid expansion of the Internet of Things (IoT) has introduced transformative capabilities in fields like healthcare, urban development, and smart manufacturing. However, the complex nature of IoT networks also exposes them to significant cybersecurity risks. This blog post explores an innovative protocol designed to address these vulnerabilities, based on the research published in “Strengthening IoT Network Protocols: A Model Resilient Against Cyber Attacks”(igmin149)【Fulltext†source】【DOI†source】.
The Current Landscape and Its Challenges
IoT devices facilitate real-time data collection and communication, forming a dense network that can be pivotal for various operations, from remote surgeries to automated industrial processes. Despite their benefits, these networks are particularly susceptible to cyberattacks due to their limited processing power and inherent vulnerabilities. Common threats include “parking lot attacks,” key dictionary exposure, and physical tampering(igmin149).
Innovations in IoT Network Security
To fortify IoT networks, researchers Guy Leshem and Menachem Domb introduced a multi-layered approach that integrates three main protective strategies(igmin149):
- Local Certificate Authority (CA) Method: This method ensures that only verified devices can join the network by requiring a certificate during the installation phase. A background daemon process continuously checks the existence and validity of these certificates. If a certificate is found to be invalid or missing, the device is disconnected from the network(igmin149).
- Securing the Key Dictionary: Inspired by the UNIX OS ‘passwd’ mechanism, this method encrypts and restricts access to the key dictionary, preventing attackers from exploiting keys even if they gain network access(igmin149).
- Detecting Missing Devices: A monitoring process pings each device periodically to ensure network integrity. If a device fails to respond after several attempts, it triggers an automatic replacement of encryption keys, mitigating the risk of compromised security(igmin149).
Implementation and Benefits
The proposed protocol employs advanced cryptographic techniques such as RSA for key generation and AES for encrypted communication between devices. During testing, a Controller device is established to manage the creation and distribution of keys securely. Devices exchange encrypted messages using shared keys that are generated and updated dynamically(igmin149).
Key benefits of this protocol include:
- Resilience Against Unauthorized Access: Device-specific certificates bolster trust and prevent unauthorized devices from infiltrating the network.
- Dynamic Key Management: The real-time replacement of encryption keys ensures ongoing network security, even if a device is compromised.
- Efficient Resource Use: The protocol is optimized for IoT devices with limited computational capacity, balancing security and performance(igmin149)【DOI†source】.
Future Prospects
The research holds promise for creating more resilient IoT ecosystems. Future directions include scaling up testing to larger networks and implementing the protocol in real-world scenarios to further refine its effectiveness(igmin149).
Conclusion
As IoT continues to shape the technological landscape, securing these networks is paramount. The protocol introduced by Leshem and Domb offers a proactive approach to counter cyber threats, paving the way for safer, smarter connectivity.
Tags: IoT Security, Network Protocols, Cybersecurity, Key Management, Encryption, Technology
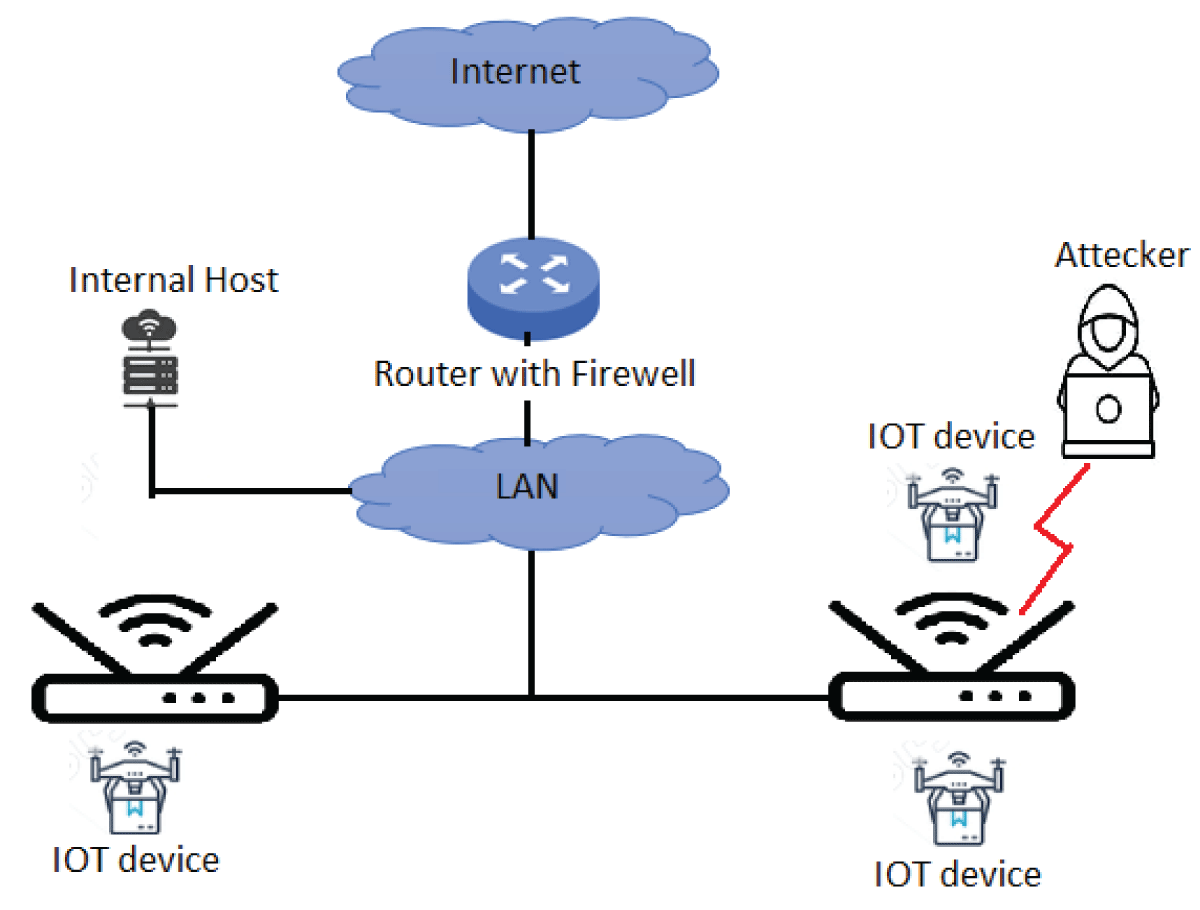
Figure 1: Demonstration of the parking lot attack.

Figure 2: Smart home concept based on IoT.

Figure 3: An example of the generated certificate for device #1.
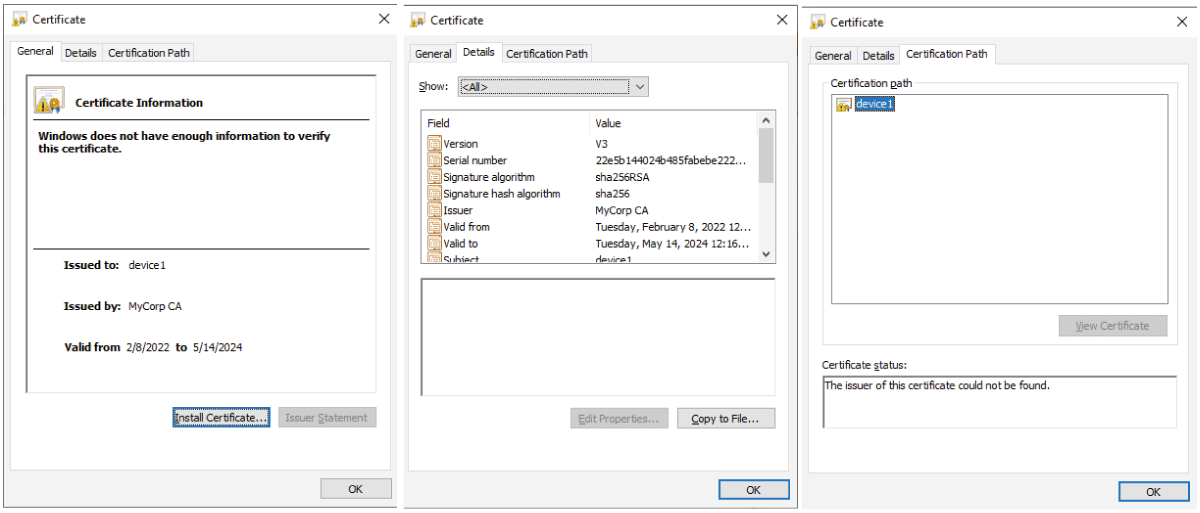
Figure 4: The Certificate of device#1 (for a sharp image, zoom in).
